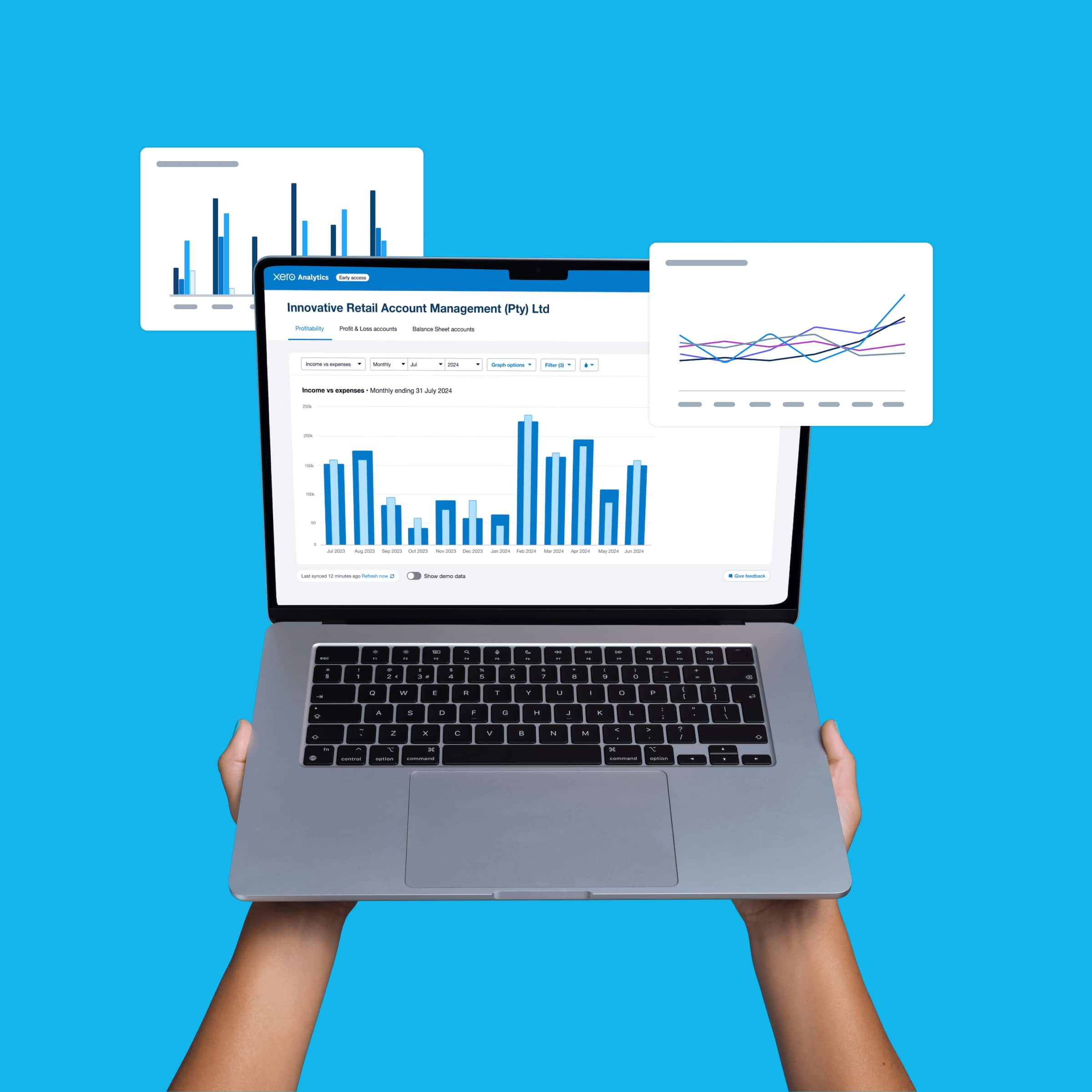
Accounting software for your US small business
Simplify your finances and get more done with Xero online accounting software.

Save yourself hours with Xero accounting software
Xero’s cloud accounting software has features and tools to help you run your small business, so you can spend more time doing what you love.
Paperless record-keeping, all in one
Centralize your finances with secure cloud-accounting software.
Features that automate your admin
Speed up your processes, from reconciling bank transactions to sending invoice reminders.
Smart data and insights
Make confident business decisions with sophisticated trend analysis and clear, customizable reporting.
88% of customers agree Xero is easy to use
*Source: survey conducted by Xero of 271 small businesses in the US using Xero, May-June 2024
All your small business accounting in one place
Xero is powerful online accounting software for US small businesses. Manage your cash flow, track expenses, accept payments online, and much more – all without leaving Xero.
- Automate tasks like invoicing and reporting
- Get up-to-date financial data for a full picture of your business
- Make your tax returns easy

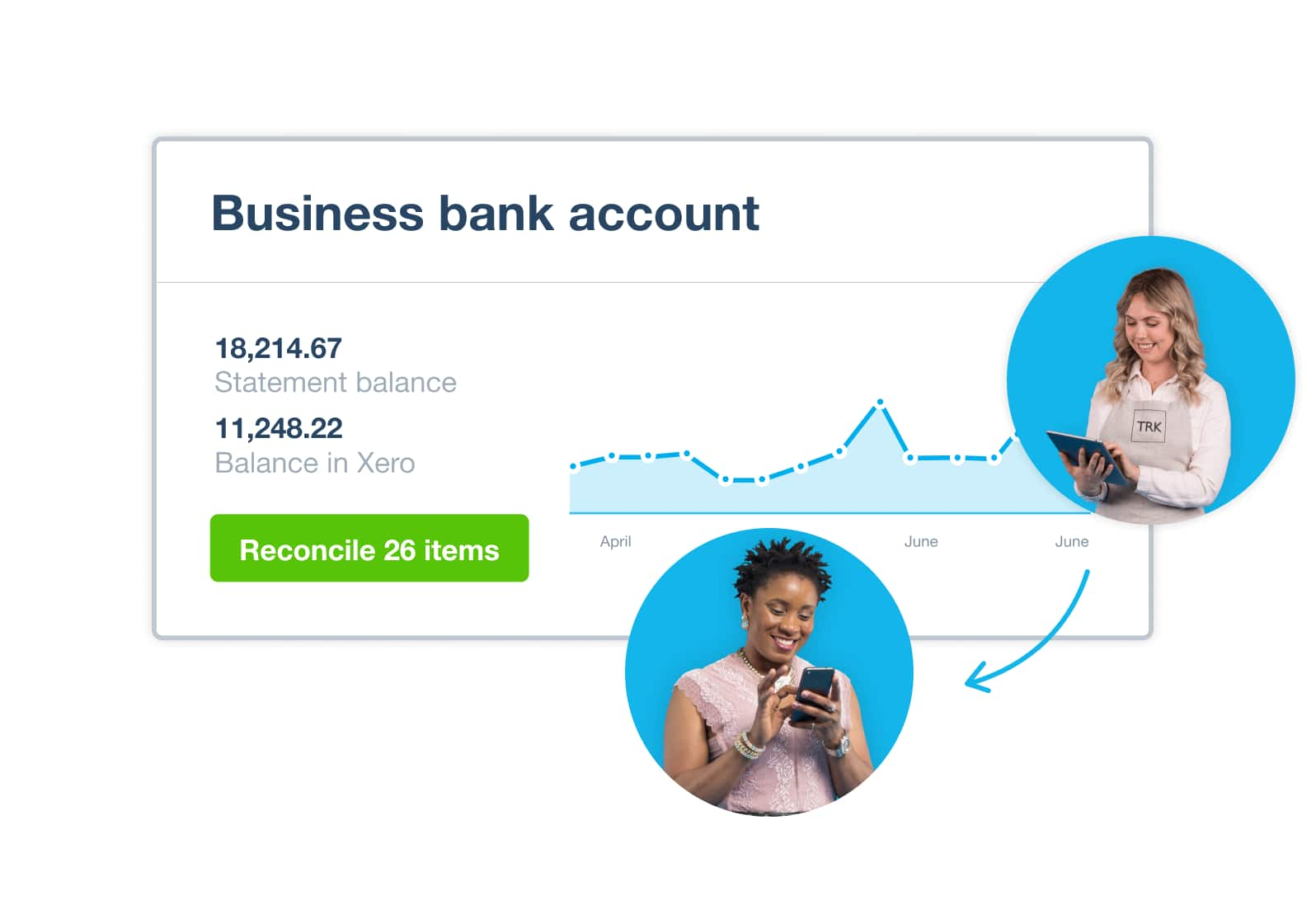
Accounting software that connects to your bank
Xero’s bank feed securely imports your transactions into the Xero accounting software each business day.
- Bank transactions automatically flow into Xero
- Reconcile your bank transactions daily
- See an up-to-date picture of your cash flow

Collaborate online in real time
Use Xero accounting software to hop online with your employees, bookkeeper, or accountant – even if you’re on opposite sides of the world.
- Access the same up-to-date financial information at the same time
- Discuss business and financial data in real time
- Allow employees to submit expenses, manage leave, and send invoices
Customizable accounting software to suit your needs
Xero small business accounting software grows with you.
- Choose a plan with the tools you need, like Xero Payroll, Xero Expenses, Xero Projects, and Analytics Plus
- Connect to third-party apps like Stripe and Vend
- Visit the Xero App Store to easily find, try, and buy apps that connect with Xero
Plans to suit your business
All pricing plans cover the accounting essentials, with room to grow.
Early
Usually $20
Now $2
USD per month
Save $54 over 3 months
Growing
Usually $47
Now $4.70
USD per month
Save $126.90 over 3 months
Established
Usually $80
Now $8
USD per month
Save $216 over 3 months
Life before Xero was a nightmare. Using a spreadsheet took a ridiculous amount of time.
Ryan is no longer dogged by paperwork.

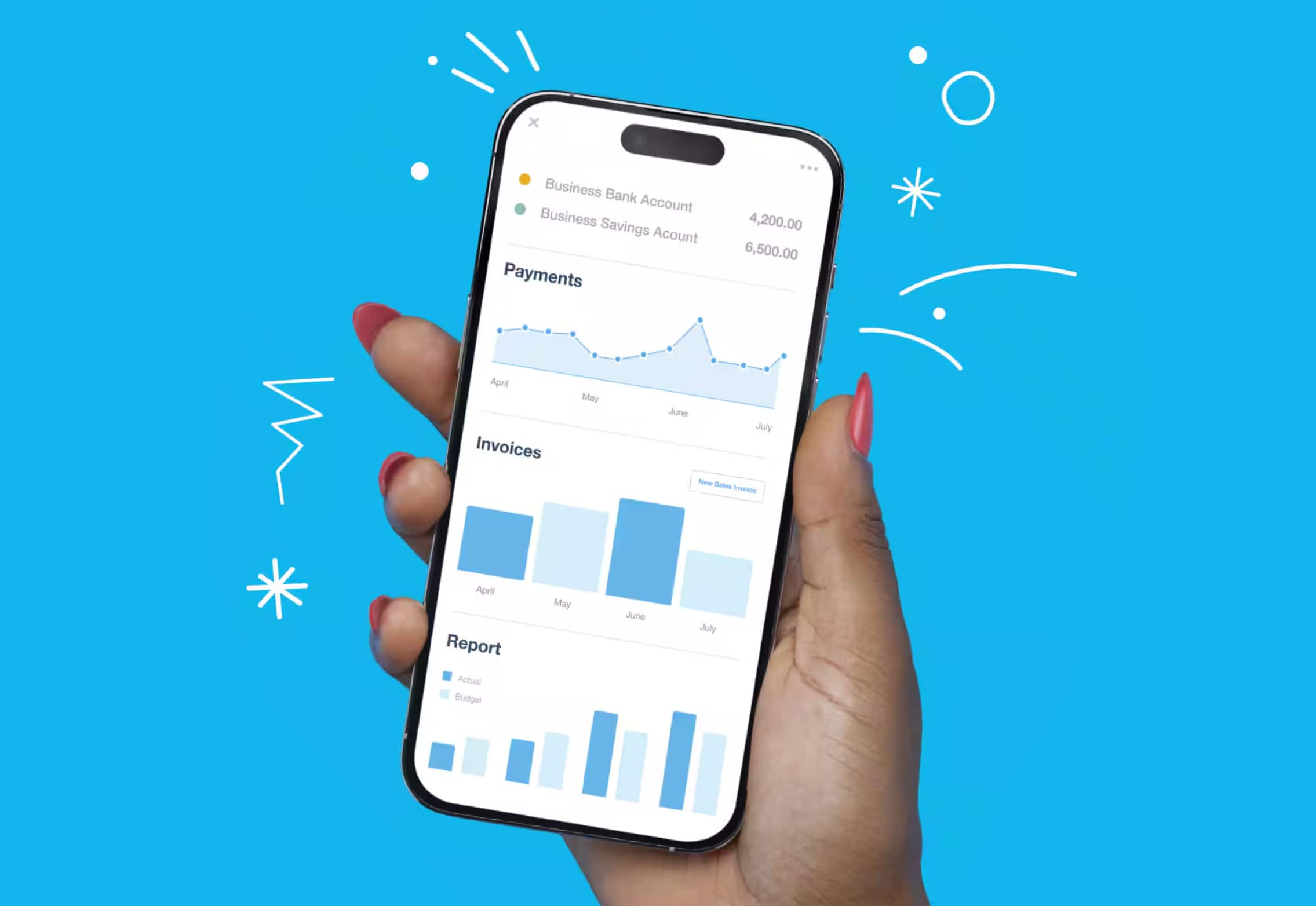
The Xero Accounting app: for businesses on the move
Financial admin needn’t pile up while you’re away from your desk. Take care of jobs with the Xero Accounting app and stay productive – from effortlessly tracking your mileage and expenses, to checking outstanding invoices. Wherever you go, the mobile app keeps your small business growing.
Get more done with the Xero Accounting app
How Xero’s accounting software works for you
Running a business can feel like you against your paperwork. Go digital with Xero – automating manual tasks and streamlining your financial admin – and win the battle!
Handle admin away from your desk
Log in anytime, from anywhere, to send invoices, pay bills, and manage your cash flow.
Simplify tax time
Filing returns needn’t be stressful. Get them done faster and comply with government regulations more easily.
Get customer support
Get help with your financial admin from experts whenever you need it.
Frequently asked questions
It’s easy to use Xero’s basic features. The software is intuitive, so people with no accounting or finance background can learn the basics quickly. It’s easy to connect your bank so your transactions flow into Xero, and to create professional invoices from scratch. Xero has all sorts of resources on business and finance topics to help, all written in plain English for when you want clear, simple answers. If you’re still unsure, Xero users can contact our support team 24/7 for help.
It’s easy to use Xero’s basic features. The software is intuitive, so people with no accounting or finance background can learn the basics quickly. It’s easy to connect your bank so your transactions flow into Xero, and to create professional invoices from scratch. Xero has all sorts of resources on business and finance topics to help, all written in plain English for when you want clear, simple answers. If you’re still unsure, Xero users can contact our support team 24/7 for help.
There are three basic steps to setting up an accounting system. The aim is to keep everything simple and accurate. First, open a dedicated business account for all your incoming and outgoing payments. Second, decide which accounting method (cash or accrual) suits your business. Third, choose accounting software, such as Xero, that has the features you need, like the ability to use eInvoicing and send foreign currency payments.
There are three basic steps to setting up an accounting system. The aim is to keep everything simple and accurate. First, open a dedicated business account for all your incoming and outgoing payments. Second, decide which accounting method (cash or accrual) suits your business. Third, choose accounting software, such as Xero, that has the features you need, like the ability to use eInvoicing and send foreign currency payments.
Technically, yes. But it can be a time-consuming process to work across different data sources and tools. Accounting software like Xero does this work for you. Xero keeps all information in one secure place, and makes automatic calculations to keep your records accurate and up to date. Because Xero is based in the cloud, you can log in at any time, from anywhere, and give your accountant and bookkeeper access so you can easily work with them on your finances.
Technically, yes. But it can be a time-consuming process to work across different data sources and tools. Accounting software like Xero does this work for you. Xero keeps all information in one secure place, and makes automatic calculations to keep your records accurate and up to date. Because Xero is based in the cloud, you can log in at any time, from anywhere, and give your accountant and bookkeeper access so you can easily work with them on your finances.
No – if you needed an accountant initially you’ll still need one. Xero accounting software helps you do your financial admin, such as bank reconciliations and managing cash flow, but it won’t replace your accountant’s advice on your specific business needs and strategy. Instead, Xero and your accountant complement one another. While Xero handles everyday financial tasks, your accountant works ‘big picture’ services and advice on your numbers, processes, and compliance.
No – if you needed an accountant initially you’ll still need one. Xero accounting software helps you do your financial admin, such as bank reconciliations and managing cash flow, but it won’t replace your accountant’s advice on your specific business needs and strategy. Instead, Xero and your accountant complement one another. While Xero handles everyday financial tasks, your accountant works ‘big picture’ services and advice on your numbers, processes, and compliance.
With your accounting software and data stored in the cloud, you can access your up-to-date accounts anywhere there’s an internet connection. You can receive automated bank feeds into your accounting software and connect to other business apps for greater efficiency. You can also collaborate with other people, like accountants and bookkeepers, by giving them access to view and share your figures. Xero regularly backs up your data and protects it with multiple layers of security.
See why online accounting is good for your businessWith your accounting software and data stored in the cloud, you can access your up-to-date accounts anywhere there’s an internet connection. You can receive automated bank feeds into your accounting software and connect to other business apps for greater efficiency. You can also collaborate with other people, like accountants and bookkeepers, by giving them access to view and share your figures. Xero regularly backs up your data and protects it with multiple layers of security.
See why online accounting is good for your businessOnce you’re set up in Xero you can import all your data from your previous accounting software, including the chart of accounts, invoices, bills, contacts, and fixed assets. We recommend you work with an accountant or bookkeeper, preferably one with Xero experience, when you move to Xero online accounting software in the US.
See how to convert to Xero from other accounting softwareOnce you’re set up in Xero you can import all your data from your previous accounting software, including the chart of accounts, invoices, bills, contacts, and fixed assets. We recommend you work with an accountant or bookkeeper, preferably one with Xero experience, when you move to Xero online accounting software in the US.
See how to convert to Xero from other accounting softwareNo, but it’s very useful. The mobile app works with Xero accounting software to help you run your small business from anywhere. Keep track of your unpaid and overdue invoices, bank account balances, profit and loss, cash flow, and bills to pay. You can also reconcile bank accounts and convert quotes to invoices. The mobile app is free with every subscription, and is compatible with iOS and Android.
See how to stay connected to your business on the goNo, but it’s very useful. The mobile app works with Xero accounting software to help you run your small business from anywhere. Keep track of your unpaid and overdue invoices, bank account balances, profit and loss, cash flow, and bills to pay. You can also reconcile bank accounts and convert quotes to invoices. The mobile app is free with every subscription, and is compatible with iOS and Android.
See how to stay connected to your business on the goCheck out the Xero App Store to find, demo, and buy business apps that connect to Xero. Apps like Stripe, GoCardless, Vend, and Shopify connect seamlessly and sync your data with Xero to make it easier to run your business.
Check out the Xero App StoreCheck out the Xero App Store to find, demo, and buy business apps that connect to Xero. Apps like Stripe, GoCardless, Vend, and Shopify connect seamlessly and sync your data with Xero to make it easier to run your business.
Check out the Xero App Store
Why small businesses prefer Xero
Across the world, people use Xero to manage their finances and control their cash flow, no matter their industry. Our accounting software is designed for small businesses and gives you flexibility, control, and visibility of your finances. Xero is used by:
- Tech startups
- Retailers
- Landlords
- Nonprofits
- Football clubs

More help with accounting software
Here’s some more guidance on accounting software tools and how they could suit your small business.
Why cloud accounting is good for business
Get your head around the benefits of accounting in the cloud.
Does your business need an accounting app?
Figure out if a mobile accounting app could help your small business.
Margin calculator
Calculate your gross profit margin with this simple calculator to check you’re hitting your targets.
FAQs about Xero in the US
Yes, Xero’s reporting and analytics capabilities help you easily prepare and submit your returns so you never miss a deadline. Your numbers will be accurate and all stored in one secure place.
See tax information for businesses from the IRS.Yes, Xero’s reporting and analytics capabilities help you easily prepare and submit your returns so you never miss a deadline. Your numbers will be accurate and all stored in one secure place.
See tax information for businesses from the IRS.Yes – Xero partners with Gusto for a full-service payroll solution. Gusto saves you time on all aspects of your payroll – including calculating employee pay and deductions – thanks to its clever automations.
Check out payroll with GustoYes – Xero partners with Gusto for a full-service payroll solution. Gusto saves you time on all aspects of your payroll – including calculating employee pay and deductions – thanks to its clever automations.
Check out payroll with GustoThe best accounting software depends on your needs. Xero’s accounting software has flexible plans so you can adjust your subscriptions to access the features you need as your business grows.
Check out Xero’s pricing plans.The best accounting software depends on your needs. Xero’s accounting software has flexible plans so you can adjust your subscriptions to access the features you need as your business grows.
Check out Xero’s pricing plans.No – Xero is based in the cloud, so all you need is an internet connection. But you need a multi-factor authentication (MFA) app to log in to Xero. MFA extra layer of security by checking that it’s really you when you log in.
Learn about data protection with Xero.No – Xero is based in the cloud, so all you need is an internet connection. But you need a multi-factor authentication (MFA) app to log in to Xero. MFA extra layer of security by checking that it’s really you when you log in.
Learn about data protection with Xero.Yes, the Xero App Store has hundreds of apps to help manage your business, including apps specifically designed for your industry and for doing business in the USA.
Check out the Xero App Store.Yes, the Xero App Store has hundreds of apps to help manage your business, including apps specifically designed for your industry and for doing business in the USA.
Check out the Xero App Store.
Get one month free
Purchase any Xero plan, and we will give you the first month free.
Useful features to run your business
Xero’s online accounting software is designed to make life easier for small businesses – anywhere, any time.